There was only one person I wanted to contact when I read the Wall Street Journal’s astonishing report that the NSA has built a surveillance system capable of spying on 75 percent of all U.S. Internet traffic: Bill Binney.
Binney is the NSA whistleblower who spent nearly 40 years at the agency developing ways to track and analyze foreign intelligence flowing over the global telecom system. That was before he left in disgust over the NSA’s unconstitutional, post-9/11 warrantless wiretapping and its corrupt relationship with contractors. “Got lots of thoughts,” Binney began, after I emailed him the Journal article this morning and asked him for his take on the story.
 Here’s key point of the WSJ piece:
Here’s key point of the WSJ piece:
The NSA, in conjunction with telecommunications companies, has built a system that can reach deep into the U.S. Internet backbone and cover 75% of traffic in the country, including not only metadata but the content of online communications.
To begin with, Binney said, that underscores everything he’s been saying all along about his former agency and its alliance with the private telecommunications industry. “They copy and store everything that the ‘Upstream’ system gets for them.” he said. What we see in the report, he added, “is the San Francisco AT&T NSA room with Narus, which copies everything on the line.”
Binney was referring to the infamous “secret room” at AT&T discovered by the technician-turned-whistleblower Mark Klein. He confirmed in 2003 what many suspected at the time: that NSA had basically set up a pipe to the U.S. Internet system and was downloading – using equipment made by Narus, now owned by Boeing – everything it could get its hands on for later analysis. One Narus device on a fiber optic line, Binney once told me, could download 1.2 million one thousand-character emails every second, or over over 100 billion emails a day. Imagine how many messages and phone calls one of those could suck up when placed by NSA at one of hundreds of telecom nodes around the country run by the likes of AT&T and Verizon (see Binney’s list of potential nodes below).
In recent weeks, the Guardian and the Washington Post have been reporting on top-secret documents leaked by Edward Snowden that largely confirm these claims. They’ve shown that the NSA downloads and analyzes huge streams of domestic intelligence obtained through court orders to telecom companies and, through software programs such as PRISM, indiscriminately collect communications records on people in the United States, the European Union, Brazil, Latin America, South Korea, Japan, India and many other countries.
It’s a privatized global dragnet – I’ve wrote about it in detail in SPIES FOR HIRE and many articles over the past five years (for the telecom-NSA angle, see in particular this piece I wrote for The Nation in 2006, “Watching What You Say: How are AT&T, Sprint, MCI and other telecommunications giants cooperating with the National Security Agency’s warrantless surveillance program?”)
The Journal report, written by the crack team of Siobhan Gorman and Jennifer Valentino-Devries, significantly advanced the Guardian and Post stories by getting former intelligence officials and former and current executives with key telecom companies to talk. The NSA, Gorman and her partner wrote, has “built a surveillance network that covers more Americans’ Internet communications than officials have publicly disclosed.” Here’s their key points:
The system has the capacity to reach roughly 75% of all U.S. Internet traffic in the hunt for foreign intelligence, including a wide array of communications by foreigners and Americans. In some cases, it retains the written content of emails sent between citizens within the U.S. and also filters domestic phone calls made with Internet technology, these people say…
The systems operate like this: The NSA asks telecom companies to send it various streams of Internet traffic it believes most likely to contain foreign intelligence. This is the first cut of the data.
These requests don’t ask for all Internet traffic. Rather, they focus on certain areas of interest, according to a person familiar with the legal process. “It’s still a large amount of data, but not everything in the world,” this person says.
The second cut is done by NSA. It briefly copies the traffic and decides which communications to keep based on what it calls “strong selectors”—say, an email address, or a large block of computer addresses that correspond to an organization it is interested in. In making these decisions, the NSA can look at content of communications as well as information about who is sending the data…
The surveillance system is built on relationships with telecommunications carriers that together cover about 75% of U.S. Internet communications. They must hand over what the NSA asks for under orders from the secret Foreign Intelligence Surveillance Court. The firms search Internet traffic based on the NSA’s criteria, current and former officials say…
In our email conversation, Binney cautioned that the court restrictions on the NSA, as limited as they are, don’t necessarily affect other agencies. The NSA, he said, doesn’t consider information collected “until someone at NSA looks at it. But that doesn’t mean that that applies to the FBI or the CIA.”
He referred me, as he has done before in discussing government surveillance, to the March 2011 testimony before the Senate Judiciary Committee of former FBI Director Robert Mueller. In that testimony, Mueller said the following in response to a question from Senator Herb Kohl about how the FBI may have missed certain information about Major Nidal Malik Hasan, the shooter at Fort Hood:
What we found as a result of the Hasan incident was that there were gaps that we had to fill. Immediately afterwards, we looked at our procedures. We found that we could do much better — a better job in information sharing with DoD [the Department of Defense, which includes the NSA]. And consequently, today elements of the Department of Defense serve on our National Joint Terrorism Task Force…
We put into place technological improvements relating to the capabilities of a database to pull together past emails as – and future ones as they come in, so that it does not require an individualized search, so putting together a technological improvement to enhance our capabilities. Lastly, we…have not just one office that is reviewing, say, communications traffic but have a redundancy of review at headquarters as well to make certain that we don’t miss something.
“Remember Mueller’s testimony, where he said with one query he can get all past and future emails as they come in,” Binney reminded me today. “Unless an NSA person looked at a U.S. email, it would not be a violation of any rule. And here again, that doesn’t count FBI or CIA or [Britain’s] GCHQ or any other of the ‘Five Eyes’ partners [which also include Australia, New Zealand and Canada] using XKeyScore to query data in the NSA storage, either for upstream collection, or data added by PRISM.”
He added that this “also applies to DHS, with their word lists for searches. And if they are using their word lists to pull data out of upstream or PRISM or any other program, it is for sure they are getting a match on just about everything.”
In other words, the NSA is downloading and storing 75 percent of all U.S. domestic Internet traffic. And analysts – many of them contractors – at the FBI, CIA, DHS and other counter-terrorism agencies get to root around in these communications for anything they deem of interest. But basically, they’re downloading it all, storing it (in Utah, for example) and then going back and analyzing it all, content included (not just metadata), and “sharing” that intelligence throughout our massive national security state.
Binney first made these arguments to me in 2012, and I was astounded. Almost afraid to know the answer, I asked him for assurance: “So you’re saying that all calls are being stored for later? We really do have a surveillance state, don’t we?” And I’ll never forget what he said in response.
My point is it’s better than anything than the KGB, the Stasi, or the Gestapo and SS ever had. Even the Chinese can’t do anything to match this, although they’re trying to get there I know. The Libyans did it. They bought some equipment from a French company to monitor all the calls in their country. Same thing: monitoring their population. The Chinese want to do it, the Syrians, all of them. This is what totalitarian states want to do. When you set up this kind of thing you are setting up the foundation for converting to a totalitarian state…People over there [at NSA] are afraid to talk about, and I don’t blame them. They have kids in college. My kids are gone. I don’t have anything to lose here. But I have a lot to stand up for. I don’t have any fear.
Today, Binney continues to speak out, without fear. His last point on the Journal report was the most intriguing.
In their Journal story, Gorman and Valentino-Devries wrote that, even before 2001, the NSA set up special Internet intercept programs “through arrangements with foreign Internet providers,” and “still has such arrangements in many countries, particularly in the Middle East and Europe.” Then, after the 9/11 attacks, “these intercept systems were expanded to include key Internet networks within the U.S. through partnerships with U.S. Internet backbone providers.” And most amazingly, “for the 2002 Winter Olympics in Salt Lake City, the FBI and NSA “arranged with Qwest Communications International Inc. to use intercept equipment for a period of less than six months around the time of the event. It monitored the content of all email and text communications in the Salt Lake City area.”
All of this is very familiar territory to Binney. Remember his last title at NSA: “Technical Director of the World Geopolitical and Military Analysis Reporting Group.” According to his bio at the Government Accountability Project, Binney “mentored some 6000 technical analysts that eavesdropped on foreign nations, collecting private phone calls and emails for NSA databases.” So he knew the technical, fiber-optic side of this territory better than anybody else at NSA. And probably still does.
In fact, Binney told me, he’d recently been studying the global fiber optic networks mentioned in the article. If he was working at the NSA, he said, he would identify “major points” in the lines “where he’d put Narus or Verint devices, or similar collection equipment to acquire most of the WWW [Internet] data. I have identified these convergent points in fiber optic lines.”
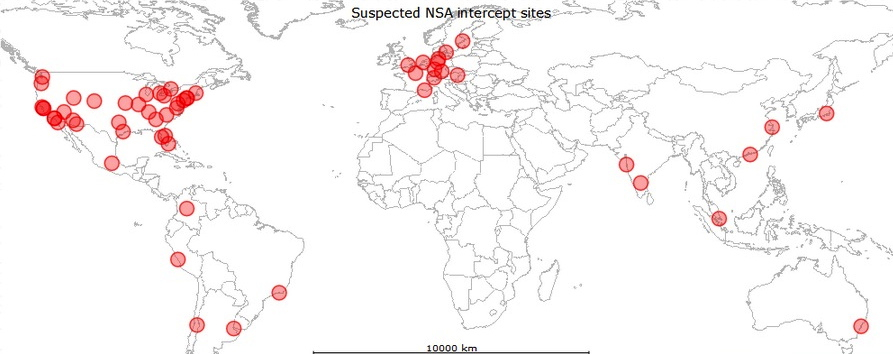
So imagine, if you will, the NSA’s global listening network, brought to you by AT&T, Verizon, BT, and Deutsche Telekom (AKA T-Mobile), as well as all those contractors (Booz Allen Hamilton, SAIC, etc.) who supply the software and analytical services. What follows, and posted on the map at the top of this story, are all the cities where your conversations – email, phone, everything – are being monitored, in Binney’s opinion. Folks, I think we have reached new levels in surveillance and privatization.
Bill Binney’s list of the most likely surveillance nodes:
AT&T — See a map of its backbone domestic network here.
Seattle, San Francisco, San Jose, Los Angeles, San Diego, Denver, Phoenix Kansas City, Dallas, Salt Lake City, Chicago, St. Louis, Nashville, Cleveland Atlanta, Orlando, Miami, Boston, New York, Newark, Washington Toronto, Amsterdam, Frankfurt, Paris, London Bangalore, Tokyo, Shanghai, Hong Kong, Singapore, Sydney
Verizon
Seattle, San Francisco, San Jose, Los Angeles, San Diego, Portland Las Vegas, Phoenix, Salt Lake City, Denver, Dallas, Houston, Kansas City St. Louis, Chicago, Atlanta, Detroit, Orlando, Miami, Charlotte, Richmond Washington, Philadelphia, New York, Boston London, Paris, Amsterdam, Tokyo, Hong Kong, Singapore
BT Group (British Telecom — North American network map)
Stockholm, Frankfurt, London 1, London 2. Seattle, Sunnyvale, Burbank, Los Angles, Salt Lake, Denver, Phoenix, Tucson, Houston, Chicago, Kansas City, Atlanta, Tampa, Washington Newark, New York, Miami Buenos Aires, Rio De Janeiro, Santiago, Lima, Mexico City, Bogota Tokyo, Hong Kong, Singapore, Sydney, Mumbai
Deutsche Telekom (which owns T-Mobile — network map)
Stockholm, Copenhagen, London, Paris, Marseille, Amsterdam, Hamburg, Hanover, Frankfurt, Nuremberg, Zurich, Vienna New York, Philadelphia, Dallas, Chicago, Los Angeles, San Francisco, Tokyo
UPDATE I: A federal judge has rebuked the NSA for “repeatedly misleading the court that oversees its surveillance on domestic soil, including a program that is collecting tens of thousands of domestic e-mails and other Internet communications of Americans each year.”
UPDATE II: Everything is fine: the NSA said this (and more) about the WSJ report:
The NSA does not sift through and have unfettered access to 75% of the United States’ online communications.
OK, then. But whatever you do, don’t ever believe this guy.